
Cybersecurity in the Automotive Industry: New Challenges for Automotive Developers
- Klaus Kainrath
- October 23, 2023
- 8-min read
The automotive industry is in a state of change. While the EU will no longer permit gasoline or diesel-fueled vehicles from 2035 onward, at the same time, autonomous driving is set to become a reality in the near future. Additionally, Cybersecurity Management Systems (CSMS) have been mandatory for all newly developed vehicle types in the EU since July 2022 – a mandate which will be extended to all new vehicles in general by July 2024. For vehicle development, these new regulations require that the topic of cybersecurity is taken into account from a very early development stage.
The term "cybersecurity" may initially evoke images of PCs and large server rooms. However, a look at the history of the automotive industry reveals how cybersecurity has grown in importance for vehicle development over the years. Since its inception in the 19th century, the automobile was, for the longest time, a purely mechanical means of transportation. Initially powered by gas, by steam or even electrically, the internal combustion engine prevailed in the 20th century [1].
The car remained something purely mechanical until the 1970s, when the first electronic control unit (ECU) was installed serially [2]. From this point onward, the number of electronic components in the vehicle increased steadily. More and more functions were supported by electronic control units, or in some cases taken over completely – security functions in particular were “electrified” quickly. The best-known functions include anti-lock braking systems (ABS), electronic fuel injection (EFI), electronic stability programs (ESP), and traction control systems (TCS).
E/E NETWORKS – The ELECTRIC/ELECTRONIC CONNECTIVITY OF VEHICLES INCREASED RAPIDLY FROM THE 80s
With more control units, the need for inter-system communication increased as well. One notable milestone was reached when the serial bus system CAN (Controller Area Network) was developed in 1983. The sum of electronic components constituted the new electric/electronic network (E/E network), which continued to grow in complexity over the years. From around 1990 onwards, the vehicle diagnostic system was introduced as well. Among other features, this system introduced a way to monitor the correct functioning of the ECUs – which can be read out without any tools via the OBD2 interface in the cockpit of every vehicle since 2004. The rapid pace of technical development has led to modern cars having up to 100 installed ECUs to date – modern cars are essentially computers on four wheels [3].
More and more important vehicle functions have been implemented purely digitally or at least digitally supported in recent years, including the accelerator pedal, the brakes, the brake assist, the electric handbrake, the electric steering assist, and the entire driver assistance system. The growing number of electrical functions requires increased wiring – for example, a contemporary mid-sized vehicle consists of up to 2.5 km of individual wire length [3].
FROM ELECTRIC/ELECTRONIC ASSISTANCE SYSTEM TO “DRIVEABLE COMPUTERS”
Many current vehicle features require a consistent internet connection – smartphone apps, WiFi hotspots, multimedia and streaming services, the automatic emergency call, and more. Many of these features need to be written in software code integrated into the vehicle by component manufacturers. As a result, a modern vehicle consists of around 100 million lines of code (LOC), a number that notably surpasses that of a Boeing 707 or even Facebook (see image 1).
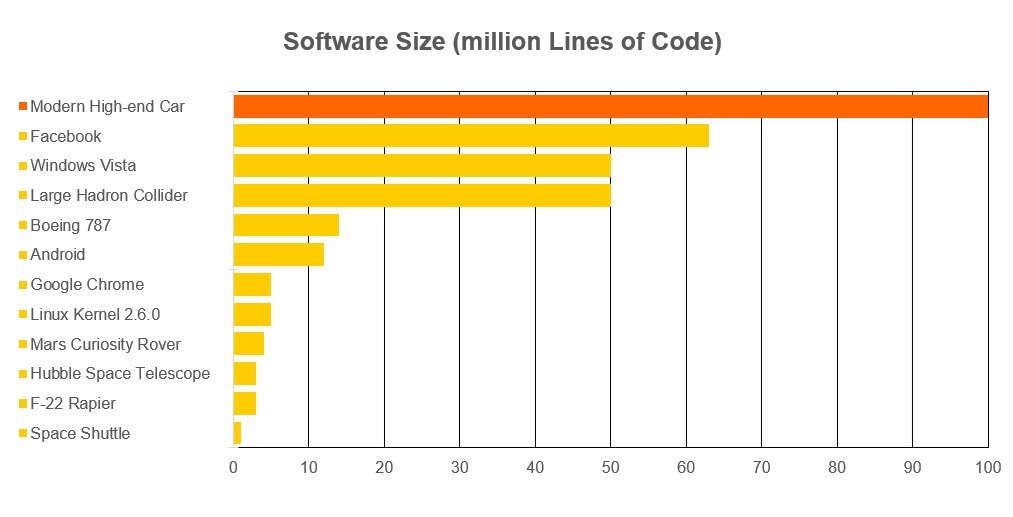 Image 1: LOC comparison between various software [4]
Image 1: LOC comparison between various software [4]
An end to this trend is far from reached. The ADAC estimates that up to 70% of individual mobility will be run autonomously by 2050 [5]. Future vehicles will become quite “talkative” in the process, as such a degree of autonomy is only possible if the entire traffic system is completely interconnected and vehicles are able to communicate with their entire surroundings. This comprehensive communication network is known as Vehicle-2-Everything communication (V2X), and encompasses cars being able to “talk” with other vehicles (V2V), the cloud (V2C), pedestrians (V2P), the infrastructure (V2I), and more. To this end, countless wireless technologies need to be integrated, creating a permanently networked vehicle with more and more communication interfaces that is "always online," so to speak.
SOFTWARE OVER-THE-AIR, ADD-ON FEATURES - HOW DRIVING BECOMES COMPLETELY DIGITALIZED
The possibility of software updates that can be downloaded to the vehicle via the Internet, i.e., "over the air" (OTA updates), is also becoming increasingly important.
On one hand, this allows vehicle manufacturers to keep their systems technically up to date without customers having to specifically visit an auto shop. On the other hand, it is technically possible to acquire add-on functions and have them activated even after the car has been purchased, generating a new source of income for vehicle manufacturers [6].
To summarize: Modern vehicles consist of up to 100 interconnected components, each with a host of software, each having a permanent internet connection, and each transmitting data via the internet to developer backends. Developers can now not only display vehicle data via smartphone apps, but also send vehicle operation commands – for example, opening the car’s windows. Automotive manufacturers inevitably become IT companies given the large amount of data stored on their servers – and subsequently, they also become prominent targets for cyber-attacks.
CYBER-ATTACKS HAVE BECOME A POTENT RISK FOR BOTH MANUFACTURERS AND PASSENGERS
Cyber-attacks in the automotive industry have been reported on the internet since the 2000s, but their frequency has grown significantly from 2010 onward – presumably due to the high degree of connectivity that vehicles had reached by then. Primarily, those attacks were restricted to radio keys. That is, until in 2015, when arguably the most prominent cyber-attack took place in a hacking conference. Two white hackers – hackers that inform manufacturers about their methods and findings after the fact – demonstrated the risk of such attacks on a 2014 SUV.
The two attackers, Charlie Miller and Chris Valasek, managed to crack the standard WiFi password in just 32 seconds. This gave them access to the multimedia control unit, the so-called head unit, where they were able to install manipulated firmware, enabling them to access the head unit via a mobile phone interface and thus via the Internet. This enabled the hackers to send vehicle-relevant commands to the vehicle over the Internet. Not only were Miller and Valasek able to activate the radio, the ventilation, or the car wash, but they could even to switch off the engine or, in special cases, deactivate the brakes [7].
EU REGULATIONS FOR AUTOMOTIVE CYBERSECURITY AND SOFTWARE UPDATES
This and other incidents, as well as the fact that the increasing number of communication interfaces continuously increases the potential attack surfaces for hackers in cars, led to cybersecurity becoming a more and more pressing issue in the automotive industry. To facilitate this emerging consumer risk, the European Union’s Working Party 29 (WP.29) developed and published specific new regulations in 2021: the United Nations Economic Commission for Europe (UNECE) R155 [8] and R156 [9].
UNECE R155 focuses on the implementation of a Cyber Security Management System (CSMS) in vehicle development – crucial systems for product development as well as incident response management throughout the vehicle lifecycle. UNECE R156 focuses on software updates, demanding a dedicated software update management system (SUMS) and regular security assessments. The regulations were adopted in June 2020 and put into effect in 2021. Since July 2022, they are required for all new vehicle types developed in the area of application (currently including 54 countries), and then for all new registrations from July 2024.
Specifically, UNECE R155 requires the following from automotive manufacturers and suppliers:
- Risk management: a company needs to implement processes for risk identification, risk assessment and risk mitigation of cyber hazards.
- Risk management must cover the entire product life cycle from development to the operational phase at the end customer.
- Monitoring of new vulnerabilities and known attacks is required to be able to react with new updates.
- A certification by an independent assessment of an accredited testing institute (for example TÜV) is needed.
UNECE R155 also specifies that in the event of cyber incidents, a response must be made by means of incident management. This means that, for example, cyber hazards (vulnerabilities, bugs) must be remedied by means of software updates. This software update process is regulated by UNECE R156.
CYBERSECURITY BY DESIGN – RISK ASSESSMENT THROUGHOUT THE COMPLETE AUTOMOTIVE LIFE CYCLE
The Society of Automotive Engineering (SAE) and the International Organization for Standardization (ISO) have also released an industry norm for automotive cybersecurity in 2021. ISO/SAE 21434 gives automotive manufacturers the means to implement CSMS in their automotive operations. It follows the principle of “Security by Design”, meaning that cybersecurity measures are introduced from early development onward. The regulations also state that CSMS should provide consistent cybersecurity monitoring throughout the entire product life cycle – meaning that cyber-attacks and security weak points should be considered from vehicle development up to its final driving mile.
To be able to assess and classify cyber dangers, ISO/SAE 21434 proposes a risk analysis similar to measures used in the IT or other industry sectors: The Threat Analysis and Risk Assessment (TARA). The TARA helps identify potential dangers based on risk assessments early in the development process and to evaluate countermeasures implemented later – as well as their effects.
Each TARA is divided into seven steps, as can be seen from the overview of Work Products 15.3 - 15.9 from ISO/SAE 21434:
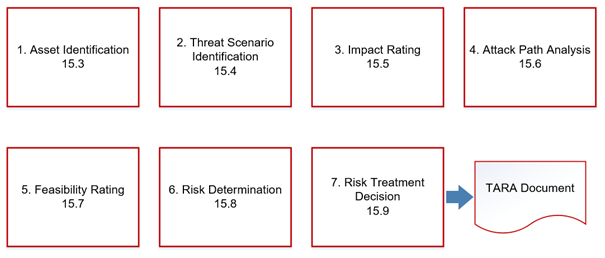
Image 3: The seven steps of the TARA. Source: Magna
These 7 steps can be further simplified into three groups:
- Identification of protection-worthy elements
- Analysis of threats and their probability of occurrence
- Risk assessment and definition of a risk mitigation strategy
The first steps include the identification of elements that are particularly worthy of protection – these so-called “assets” include selected vehicle components and functions, for example. In addition, "damage cases" for these assets and a suitable impact rating are identified (WP 15.5).
Work packages 15.4, 15.6, and 15.7 deal with the analysis of threats and their probability of occurrence. First, possible threats are identified for all damage cases identified previously. The main effort here lies in determining the probability of occurrence of those threats. There are several methods available, but the goal is always to determine the probability (feasibility) of different attack paths from a cyber-attack analysis.
The risk is then determined for each asset based on its previously defined impact and feasibility values. The method always takes the highest possible risk into account.
AUTOMOTIVE CYBERSECURITY: A CONTINOUS PROCESS OF OPTIMIZATION AND ADAPTION
Automotive businesses can verify their installed processes via an independent assessment by an accredited inspection authority, such as TÜV. This way, they can obtain a certification – and maintain it by regarding cybersecurity from the early vehicle development process onward by conducting TARAs in regular intervals to define fitting cybersecurity requirements for components development later on.
All cybersecurity requirements defined during the development phase also need to be tested and integrated. Further, a comprehensive documentation of all testing and implementation processes is necessary for obtaining a homologation (a certification for the vehicle’s cybersecurity concept). In short, without cybersecurity measures, no currently developed vehicle will be approved by the inspection authority.
Many measures known in the IT sector can also be adapted to fit the needs of automotive software. General measures such as firewalls, encoding, or access restrictions as well as automotive-specific measures such as secure onboard communication can be implemented, as long as the reduced performance of automotive components compared to “normal” IT systems is considered. Additionally, several of those measures require software encryption. As such, meeting encryption standards and the resources needed to do so should be regarded early on in component development as well.
MAGNA, AS A CSMS-CERTIFIED COMPANY, ALREADY REALIZES COMPLETE VEHICLE CYBERSECURITY CONCEPTS
Automotive supplier and development partner Magna is one of only a few companies in the world to already possess CSMS certification in accordance with ISO/SAE 21434 [10]. Its long-standing experience as a complete vehicle manufacturer enables Magna to implement cybersecurity measures in accordance with the “security by design” approach in a fast and seamless manner – throughout the complete vehicle development process and across all levels, from the complete vehicle, to system- and component-level.
Additionally, Magna already has a large network of suppliers, given its role as a system integrating manufacturing partner. As such, Magna is in constant exchange with suppliers from early development on and can discuss cybersecurity measures when they are most effective. Based on the TARA requirements, Magna determines system-level cybersecurity demands, which are then used to set the demands on a component-level, written into product specification books, and finally discussed and coordinated with suppliers. Professional component sourcing ensures that from the vehicle development phase on, cybersecurity measures are implemented stepwise into all automotive components by suppliers and then brought together into the complete vehicle board network by Magna.
When implementing cybersecurity measures, TARAs must be carried out in product development right from the start. Although the ISO/SAE 21434 standard provides general tools, the focus lies on the risk assessment of (sub)systems or components. This means that if these tools are to be applied to an entire vehicle, the CSMS must be extended to meet the demands of the many subsystems and components of a vehicle as well.
Through intensive preparations, Magna has defined the necessary processes to perform TARA on different vehicle levels. This achieves a consistent cyber risk analysis based on the complete vehicle. Subsequently, cybersecurity requirements for all planned vehicle components can be defined in a "top-down approach" which enables specific challenge viewpoints without losing track of the complete vehicle’s requirements.
HOW MAGNA ENSURES AUTOMOTIVE CYBERSECURITY WITH TARA
A TARA always looks different depending on the level at which it is carried out. Magna distinguishes between three categories:
- Complete vehicle level - consideration of the entire vehicle
- System level - consideration of subsystems
- Component level - consideration of individual components
Magna manages Levels 1 and 2 directly while Level 3 is handled by Magna’s various Tier 1 and Tier 2 suppliers (suppliers of components and components’ parts, respectively). The TARA starts at the complete vehicle level and encompasses the entire cybersecurity analysis – that is, defining assets, rating threats, and determining attack paths and probabilities.
TARAs are then implemented on system level which are based on the findings of the previous Level 1 analysis. By using the input of Level 1 consistently, Magna ensures that the risk analysis remains consistent throughout both complete vehicle and system levels.
Similarly, Magna’s suppliers are also required to conduct a TARA on their delivered components and to verify correct implementation of Magna’s requirements. Magna then integrates all components into one system and conducts all testing to ensure a seamless integration. This ensures that the final complete vehicle meets UNECE R155 regulations and subsequently receives cybersecurity approval.
MAGNA COORDINATES AND INTEGRATES CYBERSECURITY REQUIREMENTS FROM THE COMPLETE VEHICLE TO INDIVIDUAL COMPONENTS
Magna holds responsibility for a seamless and flawless integration of all individual components into the vehicle’s E/E architecture. This comprehensive task is handled by a dedicated division that specifically focuses on verification and validation of functional, as well as cybersecurity requirements.
Magna possesses specific infrastructure to do so. Testing stations enable the team to test systems, and later, the complete vehicle early on. Suppliers are continuously improving and updating their component software which incrementally unlocks more and more functions. Initially, only basic functions are tested before more specific functions are added, integrated, and later tested. By using this method, vehicle systems can be verified using contemporary testing methods which also validates the complete vehicle down the line. Primarly, Magna uses functional tests; for more demands, fuzz testing and pentesting also could be considered with external partners.
Ultimately, the automotive industry is highly affected by the rapid technological developments. The influx of more software-based features and communication interfaces all contribute to the transformation of our vehicles into large mobile computers. This change, as well as the evolving legal regulation landscape, cement cybersecurity as an integral part of automotive development processes. Magna has regocnized this trend early on; Due to the successfully certified cybersecurity management system, Magna is now the #1 partner for developing modern and, most importantly, secure vehicles.
To summarize:
Vehicles are increasingly connected with both each other and their entire surroundings. This has significantly increased the relevance of automotive cybersecurity measures. Vehicle developers are legally required to implement CSMS for their vehicles to be approved. As such, both automotive manufacturers and suppliers need to consider cybersecurity through all development processes and across all vehicle levels.
Sources:
[1] Reif, Konrad: Grundlagen Fahrzeug- und Motorentechnik, Springer Fachmedien Wiesbaden, April 2017, S. 2-4
[2] Kuhlgatz, Dietrich: https://www.bosch.com/de/stories/geschichte-der-elektronik/, zuletzt besucht 05.07.2023
[3] Hammerschmidt, Christoph: https://www.vdi-nachrichten.com/technik/automobil/automobilen-droht-der-nerveninfarkt/, zuletzt besucht 05.07.2023
[4] Busnelli, Andrea: https://www.linkedin.com/pulse/20140626152045-3625632-car-software-100m-lines-of-code-and-counting, zuletzt besucht 05.07.2023
[5] Rudschies, Wolfgang, Kroher, Thomas: https://www.adac.de/rund-ums-fahrzeug/ausstattung-technik-zubehoer/autonomes-fahren/technik-vernetzung/aktuelle-technik/, zuletzt besucht 05.07.2023
[6] Rudschies, Wolfgang: https://www.adac.de/rund-ums-fahrzeug/reparatur-pflege-wartung/reparatur-rueckruf/updates-over-the-air/, zuletzt besucht 12.07.2023
[7] Drozhzhin, Alex: https://www.kaspersky.de/blog/blackhat-jeep-cherokee-hack-explained/5940/, zuletzt besucht 05.07.2023
[8] UNECE R155: https://unece.org/transport/documents/2021/03/standards/un-regulation-no-155-cyber-security-and-cyber-security, zuletzt besucht 05.07.2023
[9] UNECE R156: https://unece.org/transport/documents/2021/03/standards/un-regulation-no-156-software-update-and-software-update, zuletzt besucht 05.07.2023
[10] CSMS-Zertifikat Magna: https://www.magna.com/docs/default-source/magna-steyr/certificates/magna_steyr_fahrzeugtechnik_iso-sae-21434-2021.pdf?sfvrsn=7a01b2a1_13, zuletzt besucht 05.07.2023
Stay connected with Inside Automotive!

Klaus Kainrath
Dr. Klaus Kainrath has been working for Magna since 2022. Since 2023, he holds the position of Cybersecurity Manager in a current vehicle project, making him the technical lead for the subject matter. Previously, he taught for 12 years at FH JOANNEUM in Graz for the departments aviation and product engineering and led numerous research projects in the areas of cybersecurity in aviation and data links for drones.
We want to hear from you
Send us your questions, thoughts and inquiries or engage in the conversation on social media.
Related Stories

The Future of UI/UX Concept Visualization in the Automotive Industry: Innovations, Challenges, and Perspectives
Inside Automotive

UI/UX Design in Vehicle Development: How Design Shapes the User Experience
Inside Automotive

Market and Industry in Transition: How a Competent Partner Can Help Navigate Challenges in the Automotive Industry
Inside Automotive
.tmb-widescreen.webp?sfvrsn=8d57edff_1)
Successfully Starting Series Production: Start-up Management in the Automotive Industry
Inside Automotive
Stay connected
You can stay connected with Magna News and Stories through email alerts sent to your inbox in real time.
